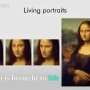
Engineering identity: Anonymous data remains vulnerable to re-identification through basic details
We create and consume data continuously. This data is specific to us, but when consolidated, this shared data can be of immense value. The value is not only for population level insights.This article is brought […]